EACCESS Erros
The Nginx Route
Project Setup
|
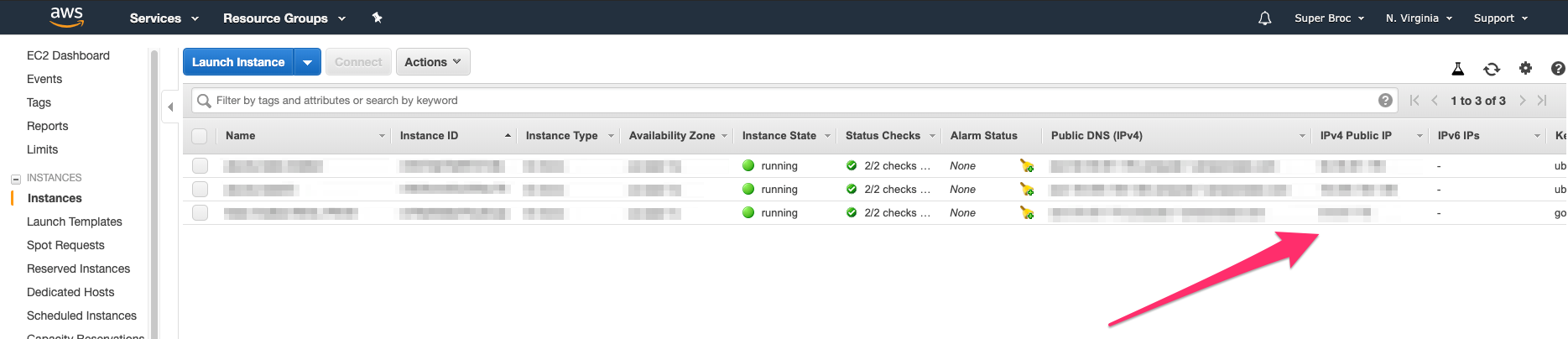
1. ssh into your server
|
ssh -i ./my-key.pem ubuntu@my-server.amazonaws.com
git clone https://github.com/myproject.git
npm start
pm2 start ecosystem.config.js --env prod
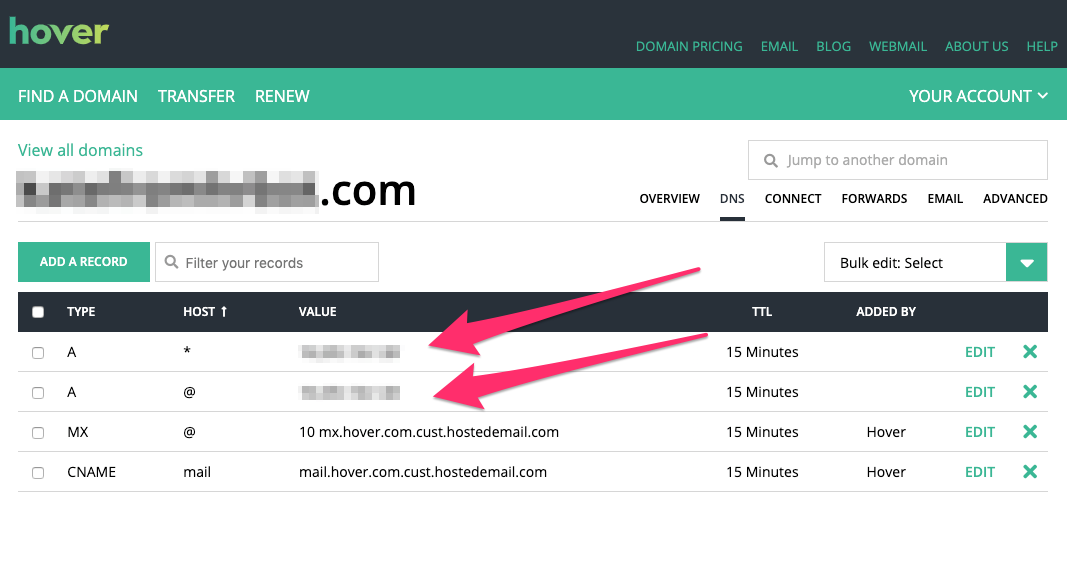
Domain Name
Certbot With --Nginx
sudo apt-get update sudo apt-get install software-properties-common sudo add-apt-repository universe sudo add-apt-repository ppa:certbot/certbot sudo apt-get update
sudo apt-get install certbot python-certbot-nginx
sudo certbot --nginx
www.mycooldomain.com,mycooldomain.com
Congratulations! You have successfully enabled https://mycooldomain.com and
https://www.mycooldomain.com
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=mycooldomain.com
https://www.ssllabs.com/ssltest/analyze.html?d=www.mycooldomain.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/mycooldomain.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/mycooldomain.com/privkey.pem
Your cert will expire on 2019-12-17. To obtain a new or tweaked
version of this certificate in the future, simply run certbot again
with the "certonly" option. To non-interactively renew *all* of
your certificates, run "certbot renew"
Botkit Specific Things
Final Tweaks To Nginx Config File(s)
sudo vim /etc/nginx/sites-available/default
server { listen 80; server_name mydomain.com www.mydomain.com; return 301 https://$host$request_uri; } server { listen 443 ssl; server_name mycooldomain.com www.mycooldomain.com; ssl_certificate /etc/letsencrypt/live/mycooldomain.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/mycooldomain.com/privkey.pem; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_prefer_server_ciphers on; ssl_ciphers 'EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH'; location / { proxy_pass http://localhost:3000; proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection 'upgrade'; proxy_set_header Host $host; proxy_cache_bypass $http_upgrade; } }
sudo nginx -t
systemctl restart nginx


 RSS Feed
RSS Feed